- info@accentucom.com
- Lansdale, PA, 19446 USA
ADFS RISK ENGINE
SphereShield’s Risk Engine module employs a set of tools designed to provide significant assurance as to the legitimacy of traffic entering the network. The Risk Engine preforms security assessments based on data such as geolocation and profiling of user behavior.
The Risk Engine plays a key role in governing access to a network, helping ensure accountability in business communication.
By assessing user details, activities, and interactions, the characteristics of connecting devices, and correlating that information using Big Data analytics, the Risk Engine is able to intelligently evaluate whether a connection is indeed legitimate.
Overview
Performing risk assessment of online activities and rendering intelligent decisions based on that knowledge, are essential in securing a corporate network. The ability to determine which transactions to allow through, which ones to monitor, and which ones to deny, is crucial in protecting against fraudulent communication attempts.
Risk Engine takes action to monitor, alert as atypical or suspicious, and—where necessary—block network traffic when a high likelihood of exposure risk, fraudulent activity,or intrusive intent have been detected.
Deploying the Risk Engine reduces exposure, protects privacy, detects impersonation, lowers occurrence of unwarranted access, and identifies trends in fraudulent activities as they occur.
Solution & Technology
The Risk Engine is a keymodule residing within the SphereShield product suite. The Risk Engine is fullyintegrated with SphereShield’s otherprincipal functions, including access control, compliance, and threat protection capabilities. The Risk Engineemploys:
- Rich Data analysis – applying advanced analytics to assess fraud patterns
- Machine learning – combining self-learning, feedback loops, scoring algorithms, and statistics
- Behavioral analysis -determining if attempted activities are typical for a particular user of the network, if they’re atypical, or even impossible
Features
SphereShield’s Risk Engine addresses the requirement to prevent fraudulent connections to a company’s network through the following mechanisms:
- Geolocation
- Displays a live map showing locations from which parties are connecting.
- Indicates from which locations failed access attempts occurred, displaying statuses on the live map.
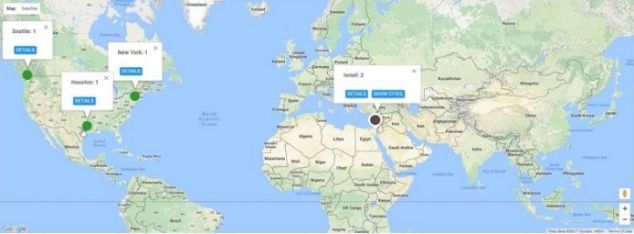
- Enriches IP data with information collected directly from users’ devices.
- Displays data details, allowing historical investigation of a specific user or IP address
- Geofencing
- Applies company-defined rules to locales that have been block-listed or safe-listed.
- Places intelligence and granularity behind fencing rules. For instance, a company can allow its salespeople and other frequent travelers to connect to the network, despite their presence in a block-listed country. Here, particular users, departments, or partner companies can be added to a safe-list.
- IP Corroboration and Scoring
- Evaluates the likely fraudulence of an IP address. This is the main criterion by which the Risk Engine determines the legitimacy of a connection attempt.
- Corroboratesgathered data with geolocation and user profile, determining whether the criteria regarding a given connection are logical and likely.
- Scores the data regarding those persons and computers connecting to a network, assigning more weight to higher-value indicators when assessing risk.
Scoring goes a long way in making Risk Engine a more powerful intrusion-preventing and fraud-fighting tool, as more attention—and greater consideration—are given to those parameters that are better predictors of malevolent activity.
- Anomaly Detection
- Triggers a security event, taking appropriate action. This could involve further monitoring, raising an alert, or blocking the suspicious traffic completely.
While the overwhelming majority of connections in a business VoIP network are legitimate, a small fraction will originate at locations that are either impossible or implausible. For instance, perhaps the “same” person tried to login from two distant locations … only a few minutes apart! Or, someone else could be attempt¬ing connection from a location that is atypical, unfamiliar, or just not geograph¬ically feasible, such as a place where a company has no customers, partners, or suppliers.
- Triggers a security event, taking appropriate action. This could involve further monitoring, raising an alert, or blocking the suspicious traffic completely.
Vision and Future
- Extendingthe Risk Engine’s user profiling capabilities, including parameters such as:
- A user’s communication participants
- Duration of use
- Type of activities, such as file transfer and desktopsharing
- Client types, for instance mobile phonesand PCs
- Extending Risk Engine’s network profiling and anomaly discovery capabilities by detecting large data capacities being transferred across a network.

Risk Engine’s main features include:
- Defining geofencing rules based on blacklists and whitelists
- Defining granular rule-based parameters such as usergroups and domains
- Displaying a map showinglive connectionsof successful logins
- Displaying a live map of login failures,indicating where intrusions could be occurring
- Analyzing user behavior, creating a profile of typical activity, in order to identify anomalies
- Blocking IPs originating in unlikely or illogical locations
- Auditing security-related events and reporting on anomalies
- Prompting security alerts in response to detection of suspicious changes in location, device, data capacity, and in reaction to atypical activity
Contact
- 642 Cowpath Rd, Suite 396 Lansdale, PA, 19446 USA
- info@accentucom.com
- +1 267 882 2558

Accentucom LLC leverages its expertise and advance technology to deliver scalable, responsive, and cost effective support services.
Copyright © 2022 Accentucom LLC. All rights reserved.
Developed by Tihalt Technologies Private Limited
